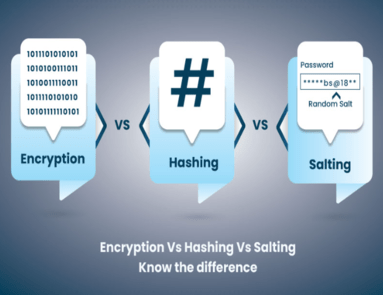
As data breaches and cyber-attacks are rising, protecting sensitive information is crucial. Hashing and Encryption are two renowned names when it comes to data protection tools. Although both safeguards data, they are different in various aspects.
This Hashing vs. Encryption blog makes you familiar with their main differences.
Before we discuss their dissimilarities, let’s learn about them.
Hashing Overview
Hashing is a procedure that transforms data into an unplanned value with the help of a hash function. It converts data into a hashed value. Thus it makes it difficult for hackers to decode it.
Hashing prioritizes the integrity of data. If you send a hashed file to someone, you also provide a hashed value with it. The recipient then calculates this value.
If the value matches, the file is not tampered with. Generally, we use hashing for large amounts of data.
How Does Hashing Work?
The hashing utilizes robust algorithms to produce hash value/function. The algorithm generates distinct hash values for different keys. In short, each unique input string has a specific hash value.
Encryption Overview
Encryption also encrypts data using algorithms. It scrambles the data so that no one, except the legit recipient, can understand it.
Dissimilar to hashing, encryption is a two-way process. First, information is encrypted and then decrypted when an intended user receives it.
Encryption is used for both sensitive and general information. The system makes your data unreadable to an unauthorized party.
How Does Encryption Work?
Encryption follows a set of rules and instructions to transform plain text into encrypted data. It helps you convert text, messages, or files into ciphertext.
The algorithm utilizes a unique information piece, known as the encryption key. This key determines how the plain text will be transformed into encrypted text. The key can be symmetric or asymmetric.
- Symmetric cryptography utilizes a symmetric key. The data sender and receiver use the same key to share the data securely.
- Asymmetric cryptography employs a public and private key. The public key encrypts information, while the private key decrypts it. In asymmetric encryption, only the private key is kept secret.
- Hybrid encryption is another encryption option. It combines symmetric and asymmetric keys. This encryption type blends the strengths of the above two encryption types.
Hashing vs. Encryption: Key Differences Based on Different Aspects
Types of Security
Hashing
Hashing focuses on data integrity. A minor change in the input data can change the hash value. People use this type of security for password storage and data integrity verification.
Encryption
Encryption prioritizes confidentiality. It aims to stop unauthorized people from accessing sensitive information.
Generally, people use it to secure communication (TLS/SSL). It protects sensitive information by converting it to an unreadable format.
Algorithms Used
Hashing
While hashing uses various algorithms, a few common ones are MD5, SHA-1, SHA-2, NTLM, CR32, and LANMAN.
Encryption
Similar to hashing, encryption also uses numerous algorithms. Some primary ones are AES, RC4, DES, RSA, and ECDA.
Reversibility
Hashing
Hashing is irreversible. It is a one-way process. It takes input data and generates a fixed-sized hash value. The primary characteristic of the hash function is that it requires only the original input from the hash value.
Encryption
Encryption, on the contrary, is reversible. It transforms readable data into unreadable data (ciphertext). It does it with the help of an algorithm and a key. The ciphertext cannot be decrypted back to the original plaintext even if the user is aware of the key.
Length Output
Hashing
Hash functions feature a fixed-length output. For instance, SHA-256 (part of the SHA-2 family) generates a 256-bit (32-byte) hash value. Due to the fixed length, hashing provides a consistent and predictable output size.
Encryption
In encryption, algorithms generate variable-length outputs based on the algorithm, key size, and operation mode. For example, in the Advanced Encryption Standard (AES), the output length varies based on key size and the mode of block cipher.
Hashing VS. Encryption: Which Should I Choose?
While the goal of both Hashing and Encryption is protection, their applications are different. If you want to keep your sensitive information safe while it is being transferred from one server to another, choose encryption.
Nevertheless, if your data is in storage and you want to protect it from hackers, hashing can be a perfect choice.
Conclusion
So this is a comprehensive comparison of Hashing vs. Encryption. This post explained how both are different in terms of various factors. All-in-all, we can say both play a pivotal role in safeguarding digital information.
Both have a different set of capabilities. Hashing acts as a firm guardian of data integrity as it has unidirectional and deterministic properties.
On the contrary, encryption transforms sensitive data into an unreadable format. Now since you are aware of their features, determine with which you should go.
The good thing is that you can combine both hashing and encryption. For example, you can use hashing to protect data on the server and encryption to protect files users download after gaining access.